Configure connections to OpenTelemetry compatible platforms
The Grepr OpenTelemetry integration enables you to ingest logs into Grepr using a Grepr source, process them with a Grepr pipeline, and then send the processed logs to any observability vendor that accepts the OpenTelemetry Protocol HTTP source (OTLP/HTTP).
To send logs to a Grepr pipeline before forwarding the logs to an OTLP/HTTP source, you change your collector configuration to send the logs to a Grepr endpoint URL instead of a OTLP/HTTP endpoint. The Grepr OpenTelemetry integration supports several OpenTelemetry-compatible collectors, including the OpenTelemetry Collector, Datadog collectors, and Sumo Logic collectors.
The Grepr endpoint URL requires a Grepr-generated token for authentication. When you create an OpenTelemetry integration, Grepr automatically generates this token for you. In the UI, the token is displayed in a dialog after you create the integration. You must copy this token and include it in your collector configuration. When you use the REST API to create the integration, the token is included in the response.
You can use the Grepr UI or REST API to add an OpenTelemetry integration. To learn how to create an OpenTelemetry integration in the Grepr UI and configure collectors to send logs to Grepr, see Use an OpenTelemetry integration in a Grepr pipeline.
To use the REST API, see the OpenTelemetry Integration specification.
Although this page describes using an integration to create a pipeline for sourcing and sending data with a single observability platform, your pipelines can use multiple integrations to source and sink data for different platforms. For example, you can create a pipeline with a Datadog integration that’s used to source data from Datadog agents, and a Splunk integration and sink that sends the pipeline output to Splunk.
Requirements
Creating and configuring an OpenTelemetry integration requires the following:
- The URL for the HTTP/HTTPS endpoint where your observability vendor accepts OpenTelemetry data.
Use an OpenTelemetry integration in a Grepr pipeline
Use the following steps to create an OpenTelemetry integration in the Grepr UI and use it in a pipeline to source and sink data.
Step 1: Create an OpenTelemetry integration
To create an OpenTelemetry integration in the Grepr UI:
-
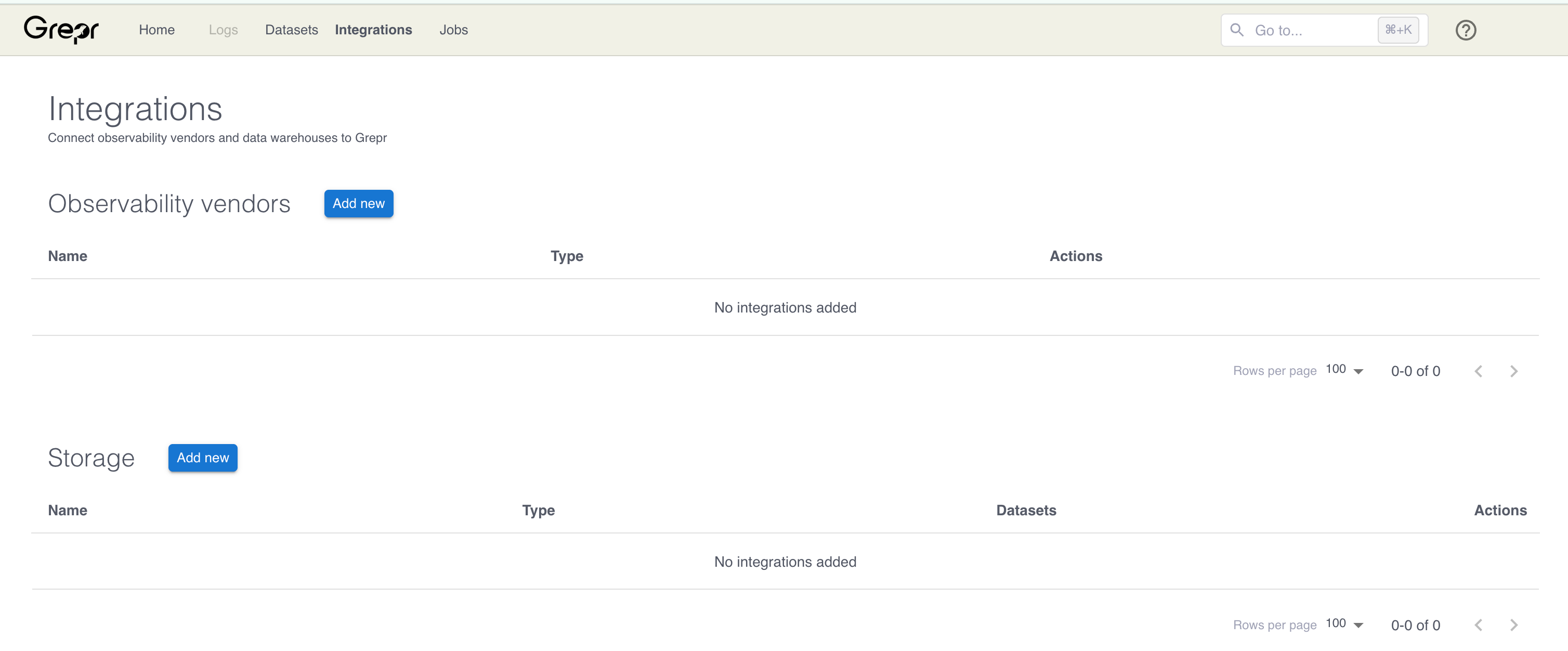
Go to the Integrations page in the Grepr UI and click Add new next to Observability Vendors.
-
In the Add Observability Vendor dialog:
- In the Type menu, select OpenTelemetry.
- In the Name field, enter a name for the integration.
- In the Endpoint field, enter the URL for the HTTP/HTTPS endpoint.
- (Optional) In the HTTP Headers section, add any required headers, such as authentication headers. For example,
Authorization: Bearer <token>orX-API-Key: <api-key>. You can optionally select Make headers secret to store the headers securely and mask them in the UI. Use this option for sensitive headers, such as API keys or tokens.
-
Click Create.
-
After clicking Create, the Grepr Token dialog appears with a Grepr-generated token. Click the Copy to Clipboard icon to copy the token. This token is required when you configure your collector to send logs to Grepr.
-
Click Confirm to close the dialog.
(Optional) Grant team access to the integration
When you have teams in your Grepr organization, you can optionally grant access to the integration to one or more of those teams. To configure team access when you create an integration:
-
In the Grant Team Access card, click the plus sign icon (+).
-
Select the team or teams that should be granted access to the integration.
-
Click Create.
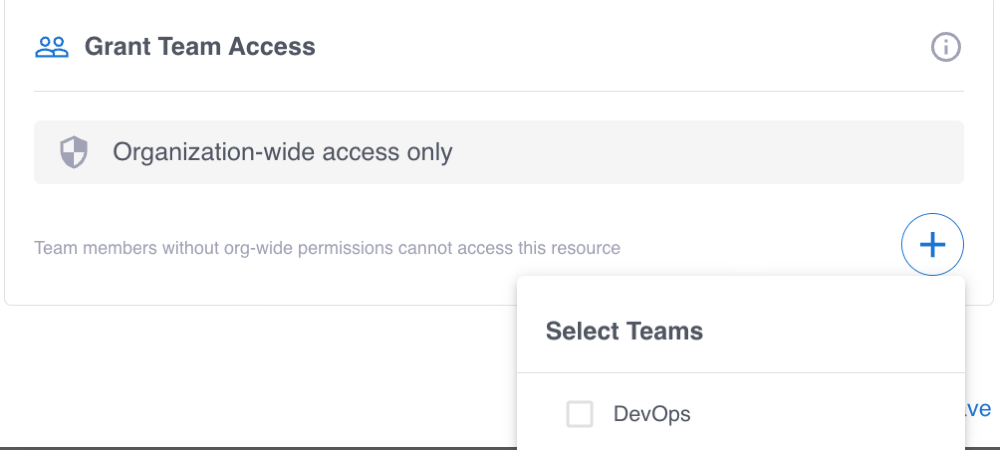
You can also add or remove teams when you edit the integration.
To learn more, see Manage teams in the Grepr platform and Permissions in the Grepr platform.
-
Step 2: Add a source to your pipeline
To add a source to your pipeline that uses the OpenTelemetry integration:
- In the Grepr UI, go to the overview page for an existing pipeline or create a new pipeline from the homepage.
- In the left-hand navigation menu on the pipeline overview page, click Sources.
- In the Add source dialog, select the OpenTelemetry integration in the Source menu.
- Click Submit.
Step 3: Configure log forwarding to Grepr
To send data to Grepr, you configure your collector or agent to send it to the ingestion URL for your Grepr integration, rather than to your observability vendor’s platform. To find the ingestion URL when using the Grepr UI to configure your pipeline, go to the details page for the pipeline, click Sources in the left pane, and copy the Ingest URL.
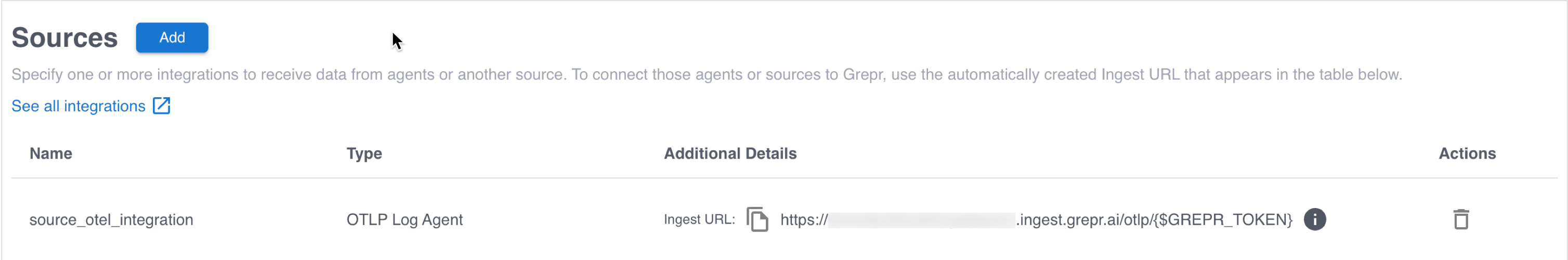
When you use the API, you can construct the ingestion URL using the following format:
https://<integration-id>-<org-id>.ingest.grepr.ai/otlp/<grepr-token>
Replace <integration-id> with the identifier of the vendor integration used by your pipeline and replace <org-id> with the identifier for your organization.
Although all sources created from the same integration share the same ingestion URL, you can use a single integration to create sources for multiple pipelines. The Grepr platform ensures events are routed to the correct pipelines.
Replace <grepr-token> with the token generated when you created the OpenTelemetry integration in Step 1.
For an observability vendor not included in this section, you can use the OpenTelemetry integration with these general steps:
-
Check your vendor’s documentation for their OTLP/HTTP endpoint URL.
-
Identify any required headers—for example, authentication headers, such as API keys or tokens.
-
Configure the integration:
- Endpoint URL: Your vendor’s OTLP HTTP endpoint.
- Headers: Any non-sensitive headers required by your vendor.
- Secret Headers: Sensitive authentication headers like API keys.
-
Configure your OpenTelemetry Collector: Use the
otlphttpexporter to send logs to Grepr’s ingestion endpoint. See the OpenTelemetry Collector configuration examples below.
To see more information and configuration examples, select the tab for your preferred log collector:
OpenTelemetry Collector
The OpenTelemetry Collector can send logs to Grepr using the otlphttp exporter. In the OpenTelemetry collector configuration (collector.yaml), set the endpoint to the ingestion URL from your OpenTelemetry integration:
exporters:
otlphttp:
endpoint: <ingestion-url>
service:
pipelines:
logs:
receivers: [otlp]
processors: [batch]
exporters: [otlphttp]Replace:
<ingestion-url>with the ingestion URL from your OpenTelemetry integration.
For dual shipping, you need to create two exporters: one to send logs to Grepr, and another to send logs directly to your vendor’s platform. Your exporter for Grepr should only include Grepr’s ingestion endpoint, with any needed headers configured in the UI. Your exporter, configured directly to the vendor’s platform, should include the endpoint for that platform and the necessary headers.
exporters:
otlphttp/grepr:
endpoint: <ingestion-url>
otlphttp/vendor:
endpoint: <vendor-otlp-endpoint>
headers:
authorization: "Bearer <vendor-token>"
service:
pipelines:
logs:
receivers: [otlp]
processors: [batch]
exporters: [otlphttp/grepr, otlphttp/vendor]Replace:
<ingestion-url>with the ingestion URL from your OpenTelemetry integration.<vendor-otlp-endpoint>with your vendor’s OTLP/HTTP endpoint URL.<vendor-token>with your vendor’s authentication token.
To learn more about configuration settings for the OpenTelemetry Collector, see the OTLP/HTTP Exporter documentation .
Grafana Cloud
To connect with Grafana Cloud via Grepr, configure your OpenTelemetry integration with Grafana Cloud’s OTLP endpoint and required authentication headers.
Integration Configuration:
- Endpoint URL: Your Grafana Cloud OTLP endpoint (e.g.,
https://otlp-gateway-prod-us-west-0.grafana.net/otlp). - Secret Headers:
Authorization:Bearer <grafana-access-token>
Your access token should be generated from a Cloud Access Policy with write access to logs. Navigate to Home > Administration > Users and access > Cloud access policies in Grafana Cloud.
In the collector configuration (collector.yaml), set the endpoint to the ingestion URL from your OpenTelemetry integration:
exporters:
otlphttp:
endpoint: <ingestion-url>
service:
pipelines:
logs:
receivers: [otlp]
processors: [batch]
exporters: [otlphttp]Replace:
<ingestion-url>with the ingestion URL from your OpenTelemetry integration.<grafana-access-token>with your Grafana Cloud access token.
For more information, see Configure connections to Grafana Cloud with Grepr integrations for detailed setup instructions including configuration examples for Grafana Alloy, OpenTelemetry Collector, and Grafana Agent.
Security Considerations
When configuring OpenTelemetry integrations:
- Use secret headers: Always use secret headers for sensitive information like API keys, tokens, or passwords.
- Validate endpoints: Ensure endpoint URLs use HTTPS for secure data transmission.
- Header validation: Grepr validates all headers for security issues, including CRLF injection, control characters, and other potential attacks.
- Avoid reserved headers: Some HTTP headers are reserved and cannot be set by users for security reasons.